SAFE Perimeter 360°
Cyber-Physical Layered Security
The SAFE Perimeter 360° tech stack delivers real-time device intelligence, enabling organizations to monitor and manage physical wireless, RF, and IoT signals and devices through a dynamic, actionable dashboard. Safe Perimeter is an advanced, AI-powered layered security platform designed to protect people, property, and critical infrastructures through advanced, wireless signal awareness.
With seamless integration into existing infrastructure, Safe Perimeter enhances security by providing data-driven cyber-physical intelligence for security and IT teams, resource officers, and first responders.
SAFE Perimeter 360°
Case Studies: What makes SAFE Perimeter 360° unique?
-
Most modern crimes involve a device — a phone, drone, or wireless emitter. SAFE Perimeter turns those digital traces into investigative leads by identifying, tracking, and attributing devices present at the scene. We can help law enforcement quickly narrow suspects, link individuals to hardware, and generate case-ready intelligence for prosecution.
-
Retail operations now depend on wireless-controlled infrastructure—access control, lighting, HVAC, camera feeds, and vendor wifi systems. RF interference or compromise could cause:
Unauthorized system takeovers or disruptions.
RF jamming that disables IP security cameras.
Drone-initiated payloads targeting Wi-Fi access points or GPS receivers used in logistics.
Cyber-physical sabotage risks safety and public trust.
Benefit: AirShield detects anomalous behaviors and interference across all RF layers—including hidden IoT or OT signals—while SkyShield defends against aerial vectors targeting those systems. Together, they form a zero-trust wireless perimeter around the area, preserving operational uptime, incident traceability, and readiness for coordinated response.
-
In high-density environments, attackers can exploit wireless vectors to trigger panic, confusion, or diversion. Threats include:
Drones flying over fans or players, triggering fear.
Fake cellular towers or spoofed alerts are disrupting patron communications.
RF interference disrupts emergency radios or PA systems during a crisis.
Panic can escalate quickly in tightly packed crowds, and traditional security often lacks visibility into RF-based attack methods.
Benefit: AirShield monitors for RF anomalies across zones, while SkyShield secures the airspace. Both systems are cloud-connected for real-time alerting, mobile response coordination, and automated incident logging—giving security time and data to act decisively before threats impact safety or reputation.
-
Public Areas are flooded with personal and unauthorized RF devices—Flippers, rogue hotspots, Bluetooth skimmers, fake access points, and embedded surveillance tools to scam the public. These can be exploited for:
Credential theft via spoofed Wi-Fi portals.
Hidden RF bugs in Executive / VIP Areas, etc.
Bluetooth-based Contact tracing and Access Control manipulation.
Unmanaged devices often evade traditional security tools, creating blind spots that can compromise privacy, compliance, and safety.
Benefit: AirShield provides continuous, passive visibility across Wi-Fi, Bluetooth, Cellular (4G/5G), and more, identifying both managed and rogue devices. The system logs threat behaviors and integrates with SIEM/SOAR platforms for automated response, giving security teams actionable intel to eliminate wireless vulnerabilities without disrupting the patron experience.
-
Public Spaces are prime targets for unauthorized drones used for surveillance, livestream piracy, or even the delivery of malicious payloads. Scenarios include:
Drones hovering for espionage or media leaks.
Unauthorized aerial footage broadcast to pirate streaming platforms.
Drones dropping propaganda, pathogens, drugs, or smoke devices, or triggering panic.
Benefit: SkyShield Drone Detection provides continuous, passive drone detection via RF for over 450 drone types, including tethered drones. Most stadiums ban drones during events, and a single airborne intrusion can compromise safety, intellectual property, or halt operations. away using 360° RF monitoring, classifies 450+ drone types (including DIY), detects drones up to 4.5 miles away, and uses selective jamming* to neutralize threats without affecting adjacent RF systems. Real-time alerts and drone flight-path tracking give property operators control of their airspace and confidence in their security response.
SAFE Perimeter Professional Security Products & Services
SAFE Perimeter delivers high-performance technology integrations and protective security teams for mission-critical environments. As a boutique but scalable provider of signals intelligence and C-UAS defense, we work with leading vendors, licensed risk assessors, and top security firms to provide best-in-class security technology.
Safe Perimeter leverages existing security infrastructure and is not a rip-and-replace solution by seamlessly integrates software with existing infrastructure.
"This solution gave our training facility unprecedented awareness across the entire footprint, and we love working with the NFL family—enhancing secure office operations and player and visitor safety.
We are actively recommending SAFE Perimeter to high-profile individuals, teams, and league sports partners."
— 🏈 Director of Security, NFL Team
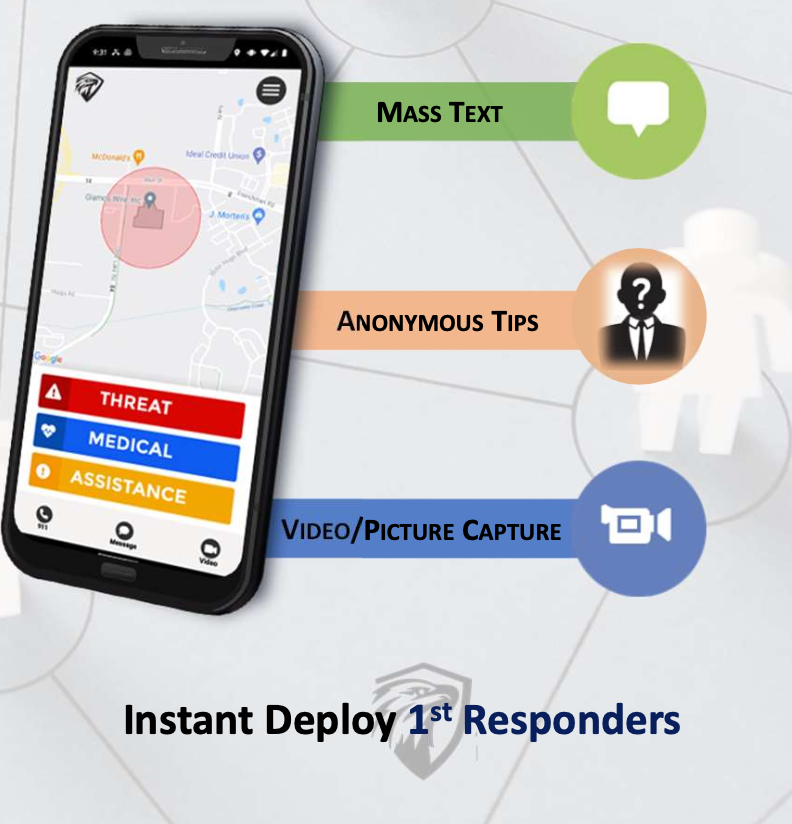
ALERT-COM® CRISIS & Emergency System
SAFE Perimeter proudly resells and deploys ALERT-COM® — Alert-Com Mobile rapid notification and communication platform for emergencies such as active threats, medical situations, anonymous tips, general assistance, severe weather updates via secure, encrypted servers. ALERT-COM® integrates seamlessly with layered security ecosystems and can be remotely managed and configured via the companion app for Android or iOS.
SAFE Innovation
Revolutionizing situational awareness intelligence with passive and proactive solutions.
-
Keeping people safe in public and private venues requires more than cameras and guards; it demands visibility into the invisible, a 360° SAFE Perimeter. We are integrators at our core and specialize in technology for events and public spaces, including Counter Unmanned Aerial Systems (C-UAS) with with AirShield® and SkyShield®.
-
Sensors connect to a proprietary Machine Vision Cloud. Optional server installation is available. Receive real-time and actionable results via a customized dashboard and easily integrate into daily operations and existing infrastructures.
-
Identify unacceptable wireless IT, IoT, and OT on managed and unmanaged devices, things, and networks, including an incident response loop.
Software-Defined Radio monitors the new WiFi 6 and 5G spectrum (300 MHz to 6 GHz) to detect emerging and advanced wireless IoT threats and provide a 360-degree situational awareness. Additionally, edge-based risk management can use AI and ML-based methods for asset discovery, classification, and risk profiling with blacklists / whitelist options and maps.
-
Leverage SAFE Perimeter for the growing IT, IoT, and OT security risks with real-time maps and dashboards for an additional layered cyber-physical security solution: the industry’s leading wireless/RF security measure.